Table of Contents
- INTRODUCTION
- WHAT IS USAM RANSOMWARE
- HOW RANSOMWARE ENTER OUR SYSTEM [OPERATING SYSTEM]
- HOW TO REMOVE RANSOMWARE [USAM]
- HOW TO REMOVE RANSOMWARE [USAM][MANUALLY]
- REMOVE THE INFECTION CREATING FILES/SERVCES
- RECOVERING THE DATA ENCRYPTED BY THE RANSOMWARE
INTRODUCTION
If you have ever suffered an infection of your windows with ransomware, you must be acquainted with the horror it creates when we are not able to use any of the file, videos, audios, .data file and most of the useful files containing our useful data.
I just got infected with this ransomware and luckily could recover all my data. This is the reason that I am writing this article to help all my friends out there to be able to recover their valuable data.
In this article we will discuss what is ransomware, how it infects, how to remove this and how to recover the data already encrypted.
WHAT IS USAM RANSOMWARE
First of all let us understand what is a RANSOMWARE.
Yes! you are correct. It is concerned with the RANSOM.
RANSOMWARE IS A VIRUS, WHICH WILL COME TO YOUR COMPUTER AND GET EXECUTED [ OBVIOUSLY WE WILL START IT BY MISTAKE] AND
ENCRYPT ALL YOUR DATA FILES LIKE FILES, VIDEOS, AUDIOS AND GIVE IT AN EXTENSION .USAM [OR ANY OTHER AS PER THE RANSOMWARE].
NOW, AS THE FILES ARE ENCRYPTED [ENCRYPTION MEANS CHANGING THE DATA WITH A SECRET KEY AND MAKE IT UNUSABLE] , WE WON’T BE ABLE TO USE THEM. A NOTE IS LEFT WITH THE VICTIM IN WHICH
THE PEOPLE BEHIND THE RANSOMWARE ASK FOR THE MONEY FOR THE DECRYPTION.
ENCRYPTION used in RANSOMWARE is quite difficult to crack unless the correct UNIQUE KEY for the decryption is available.
Don’t pay ransom and please try the methods discussed here which might help you.
USAM RANSOMWARE is similar to few previous ransomware like nypd, zorab, zwer etc.
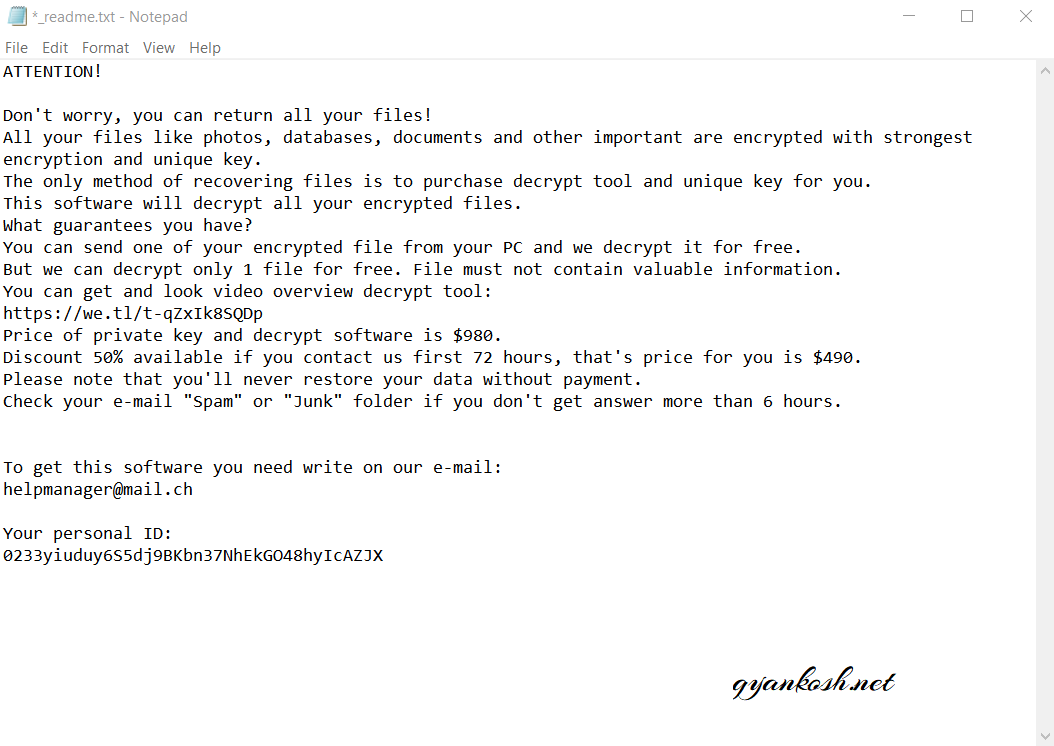
Here is the sample of the NOTE which I received.
ATTENTION!
Don’t worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-qZxIk8SQDp
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.To get this software you need write on our e-mail:
helpmanager@mail.chYour personal ID:
0233yiuduy6S5dj9BKbn37NhEkGO48hyIcAZJXvBIEZrvzXG1yyPt1
AS I HAVE | SHOULD WORK FOR YOU TOO .KINDLY TRY ONCE
HOW RANSOMWARE ENTER OUR SYSTEM [OPERATING SYSTEM]
To corrupt our system with the virus , it needs to enter our system and get executed [run].For this, the culprits use very lucrative methods. For example, they can send you a very SERIOUS LOOKING email having the link, or any message containing the link, or keep their virus inside the file or software which you download from any link.Most of the times, we get affected by these when we download any file from the insecure source such as torrents.As , we are very excited about the enjoyment using any game or software or audio or video etc. , they take advantage of this , and serve us their deadly virus.We download the file, execute it and it corrupts our system. This is a frequent way of infecting people using the ransomware or any other virus.
IF WE BECOME A LITTLE CAREFUL ABOUT CLICKING LINKS AND VISITING ONLY RELIABLE SITES, THERE ARE MEAGER CHANCES OF GETTING INFECTED.
HOW TO REMOVE RANSOMWARE [USAM]
Now, we are in a situation , when the system has been inefected and we have no access to our data. So we have following future actions.BE SURE TO REMOVE THE MALWARE[VIRUS] FIRST OTHERWISE IT’LL AGAIN ACT ON OUR DATA AND THE RECOVERY WILL BECOME HARD FOR US.
1. REMOVING THE INFECTION OF THE VIRUS USING AN ANTIMALWARE.
2. REMOVE THE INFECTION CREATING FILES/SERVICES. [MANUALLY]
3. DECRYPT THE DATA.
1. REMOVE THE INFECTION OF THE VIRUS USING AN ANTIMALWARE
ANTIMALWARE is a program designed to find and stop the processes which are harmful for our pc. The companies which offer these softwares are vigilant about the threats in the market and put those in the updates offered for those software.The software scans our systems and finds out the programs or processes which are creating the problems or which are similar to the definitions fed to them.After recognizing the culprit services, they take the file and quarantine them or delete them as per our choice. [ Software normally asks for our permission before deleting].So it was a brief working of the Antimalware or antivirus.There are many antimalware available in the market, but at the time of panic we don’t have that much time to find out which one is best for us. This is when we need others’ advice.I am enlisting two famous antimalware here, with which I have my own experiences.
A.EMSISOFT ANTIMALWARE HOME
B. MALWAREBYTES.
Both of these antimalware softwares are available for a trial so you need not to purchase them immediately. Yes, if you like them you should buy one for sure to avoid yourself for being in similar situation in the future.Let us find out how to use them one by one.
A. Emsisoft Anti-Malware Home
It is an antimalware offered by EMSISOFT and they provide a full trial for 30 days. It is really a good antimalware and is very active to find out the programs which can cause us problems. It is going to keep you safe always.
For now, we need to find out the ransomware which is creating us problem so start the process by downloading the software.
DOWNLOAD LINK: https://www.emsisoft.com/en/home/antimalware/#scan-and-clean
- The link would land you up on the download page of the EMSISOFT ANTIMALWARE which they have named as SCAN AND CLEAN.
- Click FREE 30 DAY TRIAL.
- The next screen would ask you for signing up.
- You can sign up easily by giving up your email id or directly by facebook or gmail account.
- After signing up, it’ll ask for a secure code which has been sent to you on your email.
- Put the code in the given field.
- Click OK.
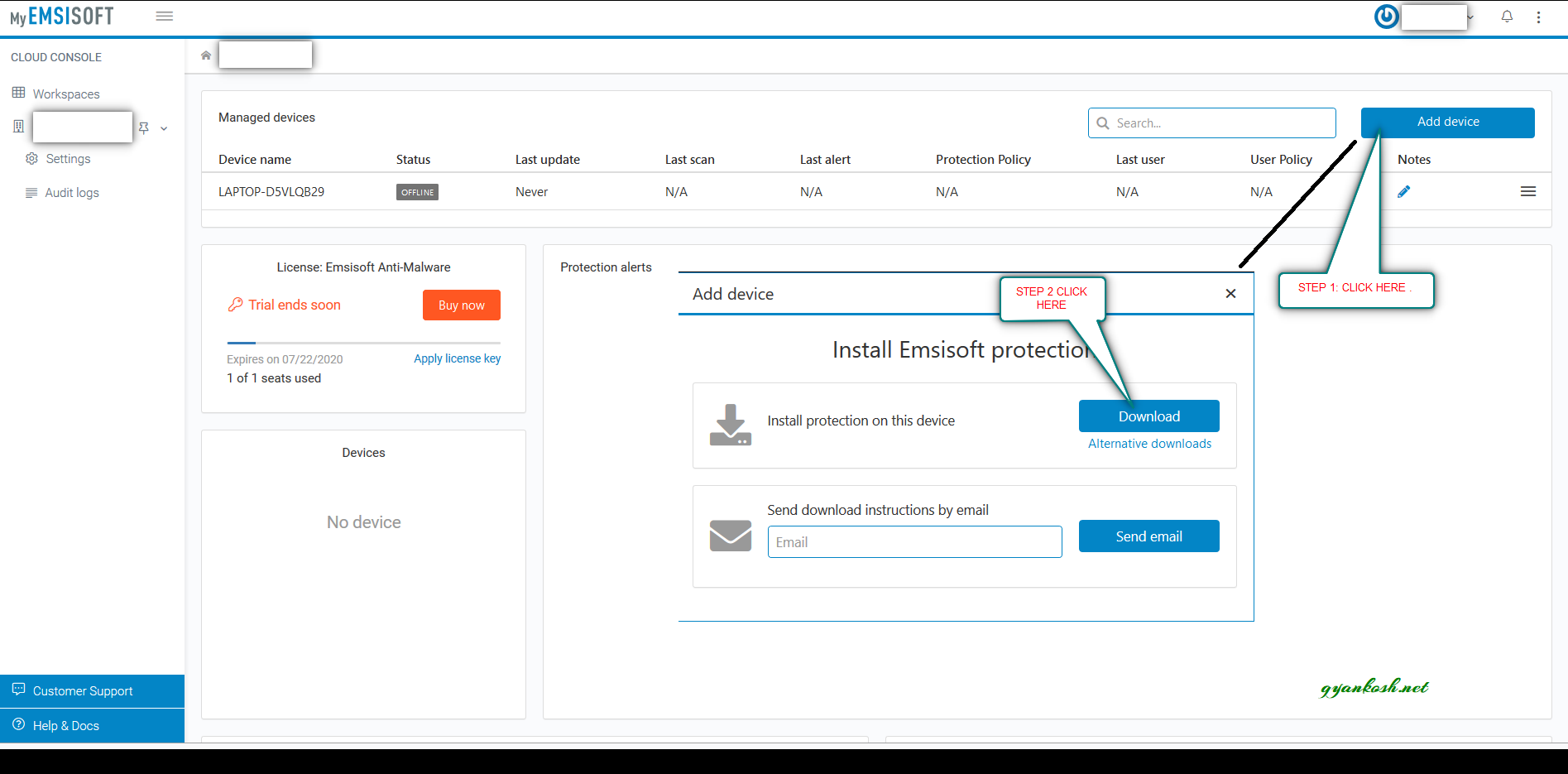
- We ‘ll enter in the cloud console of emsisoft as shown in the picture below.
- Click ADD DEVICE. A small window will open.
- Click DOWNLOAD as shown in the picture above.
- After clicking the DOWNLOAD , a small window will ask to save the software.
- Click SAVE FILE.
- After the file is downloaded.
- Click the file to run.
- It’ll ask if you want to allow the software to make changes, click YES.
- After this, the download of the main application will start.
- Let it complete.

- After the download is complete, the application will start to install. Let it install.

- After the installation the homescreen of the application would open.
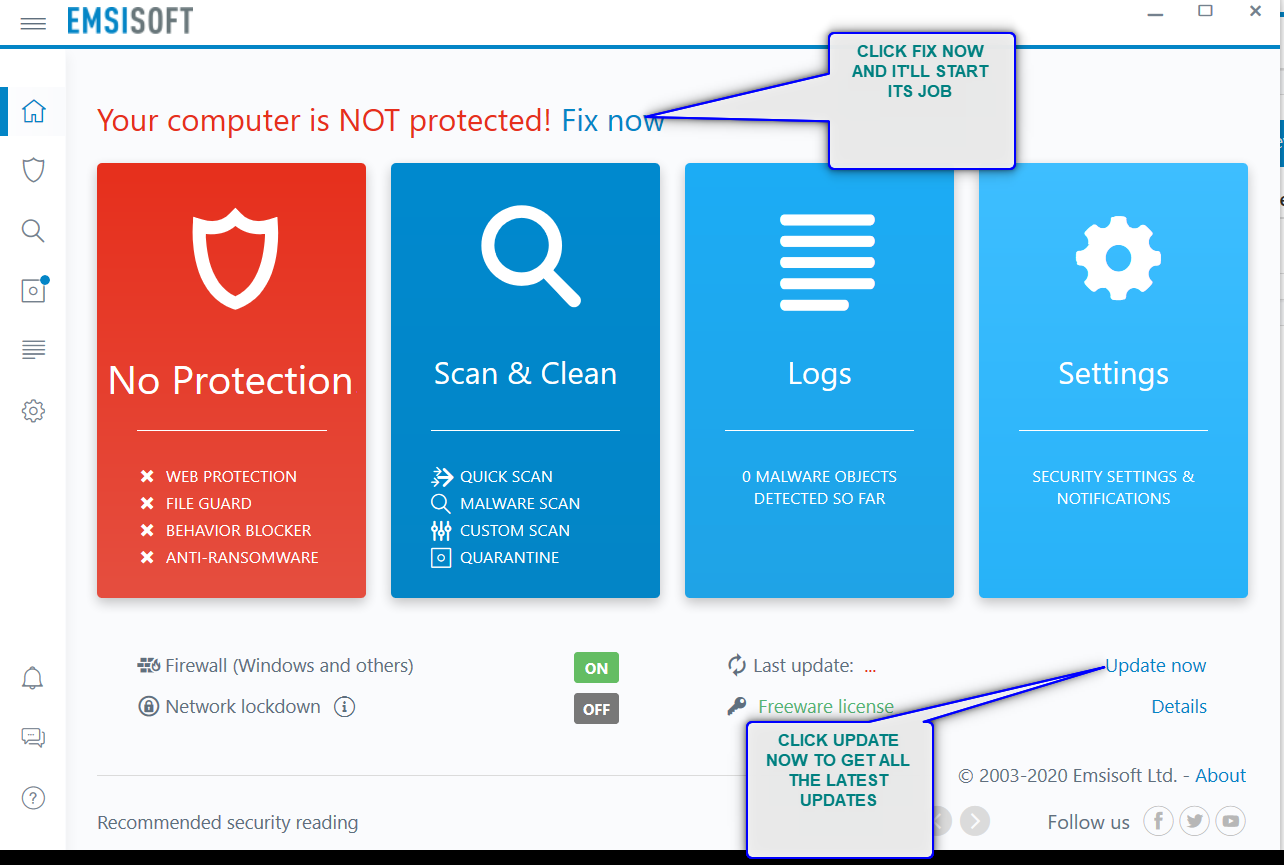
- Click UPDATE NOW.
- Click FIX NOW and the protection will start the scan and save you from further damage.
- It’ll find out the culprit files and quarantine them. Delete them if it asks. After this, go for the decryption procedure.
- CHECK OUT THE PICTURE BELOW. A LOT OF INFORMATION IS PROVIDED IN THE SAME.
2. MALWAREBYTES

It is our second choice for removing the ransomware and saving ourselves in future. It is also a good application which works effectively in keeping the malware out of our windows. Follow the steps to use this application.
First of all, let us download the application.
DOWNLOAD LINK:https://www.malwarebytes.com/mwb-download/
FOLLOW FURTHER STEPS TO CONTINUE
- After clicking the download link, you’ll reach the following screen.
- Click DOWNLOAD FREE under FOR HOME section.
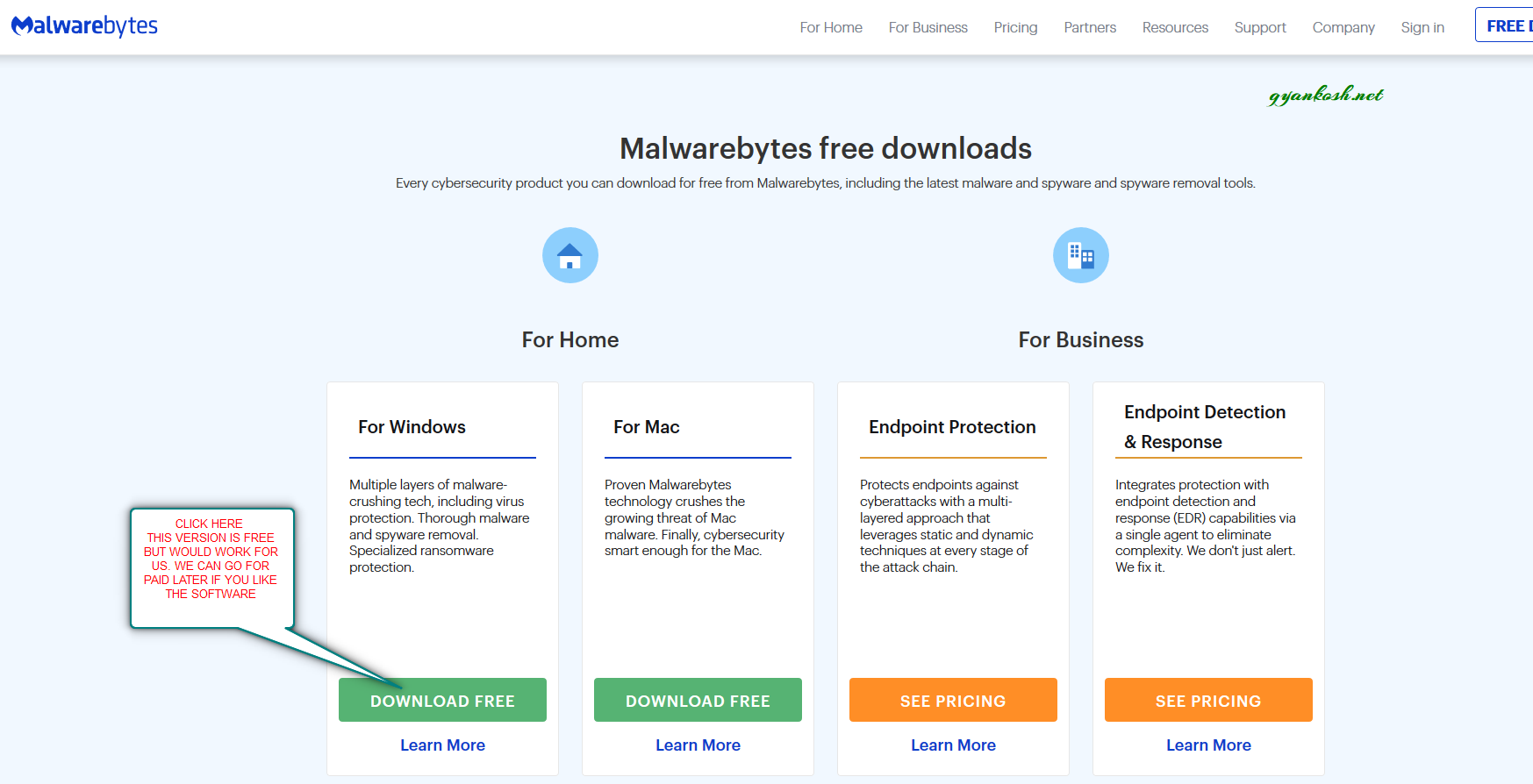
- After clicking the DOWNLOAD FREE button , a download option would appear.
- Click SAVE FILE.
- After the file is saved, go to the file location and double click the file.
- Windows would ask if you let the application to make changes, click YES.
- The following screen will appear. Choose the option which applies to you.
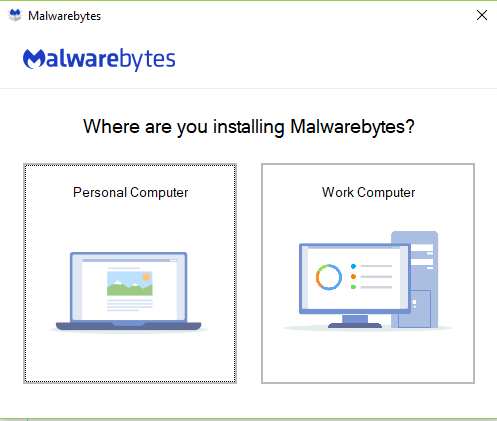
- I chose, Personal Computer.
- Click Install.
- The program will start installation. It will download files too, so an internet connection is needed. Make sure a good connection is present.
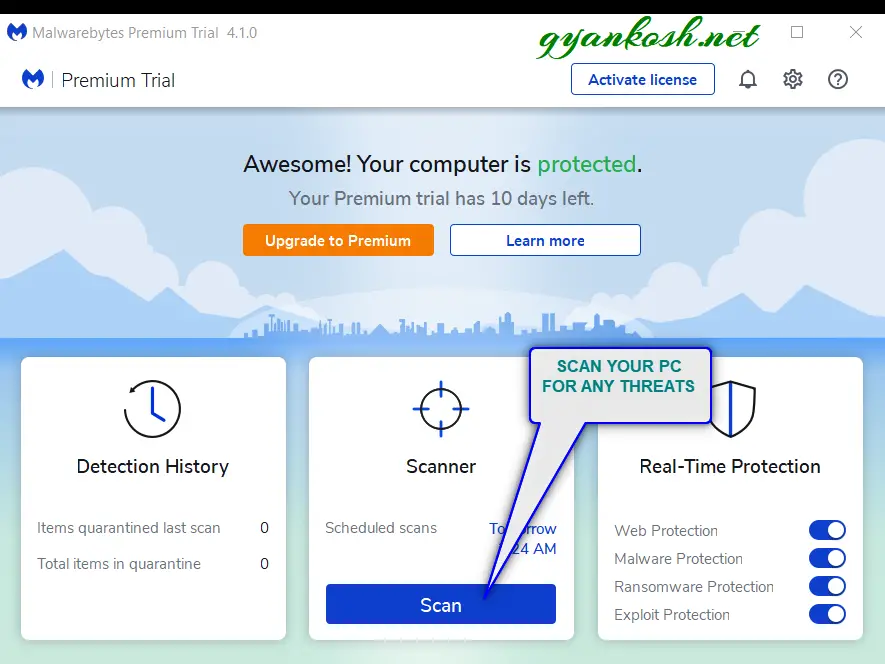
- After the installation the control center of malwarebytes will open as shown in the picture below.
- Press SCAN as shown in the picture above and let the application scan the system to find out the faults.
- Once done, clean the culprit files and do the decryption .
HOW TO REMOVE RANSOMWARE [USAM][MANUALLY]
REMOVE THE INFECTION CREATING FILES/SERVCES
Our all data has been infected which means certain services are active, which are affecting our data.So , we need to stop such services.It can be tried, but some services won’t be stopped or the services are created in such a way that once you stop any service, the other one would start it.To get rid of this, we have one option to start the pc in a safe mode. SAFE MODE of the pc only allows the basic services which are necessary to sustain the operating system. So let us start the process.
BEFORE STARTING THE PROCESS, USER OF THIS WEBSITE IS ALWAYS ADVISED TO KEEP THE BACKUP OF ALL THE DATA. THE PROCESSES CONTAIN SOME STEPS TO INTERVENE DIRECTLY WITH THE SYSTEM FILES, WHICH CAN BE HARMFUL FOR THE USER IN ANY WAY.
IT IS SOLELY DEPENDENT ON THE WISH OF THE USER TO CONTINUE OR NOT AND GYANKOSH.NET IS NOT RESPONSIBLE IN ANY MANNER FOR ANY KIND OF LOSS OCCURRENCES.
STEP 1: RESTART COMPUTER IN SAFE MODE
- Press WINDOWS KEY+R, which will open RUN COMMAND.
- Type “msconfig” in the field and press OK.
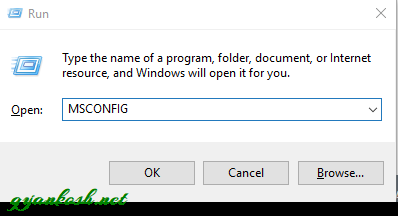
- A prompt will open from the windows “ASKING THAT IT IS A SYSTEM UTILITY. IF YOU WANT TO CONTINUE. ” PRESS YES.
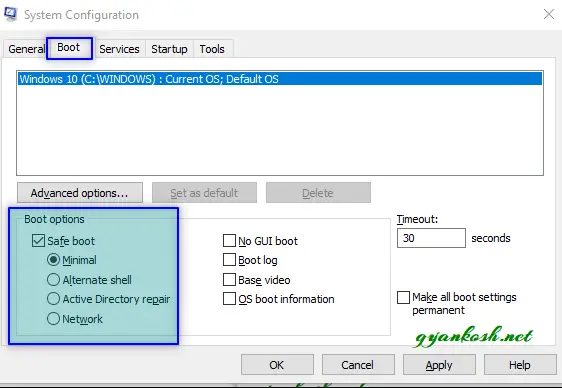
- In the system configuration dialog box, go to BOOT TAB and go to BOOT OPTIONS [marked in the picture below].
- Check SAFE BOOT and choose MINIMAL.
- This command will open the SYSTEM CONFIGURATION dialog box.
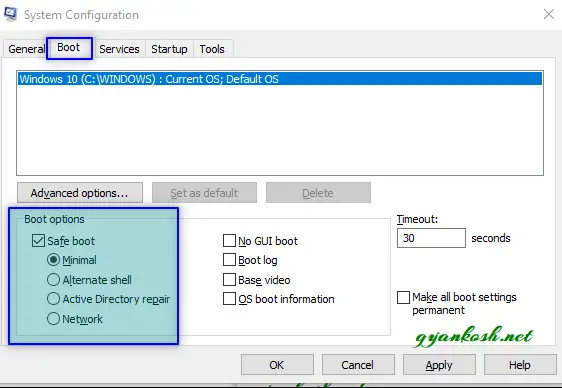

- Click APPLY.
- Following dialog box will appear.
- Click RESTART.
- The SYSTEM will restart with the safe mode.
- The wallpaper in the desktop will contain the word SAFE MODE as shown in the picture below.

STEP2: CHECK THE PROGRAMS INSTALLED IN THE SYSTEM.
- Press WINDOWS KEY+R, which will open RUN COMMAND.
- Type “appwiz.cpl” in the field and press OK.
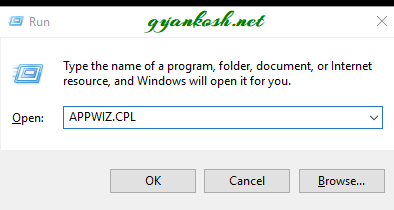
- It’ll open the PROGRAMS UNINSTALL OR CHANGE A PROGRAM.
- Scan the programs names. Find out the suspicious installations which has taken place.
- An easier way is to sort the programs as per the INSTALLED ON date as shown in the animation below.
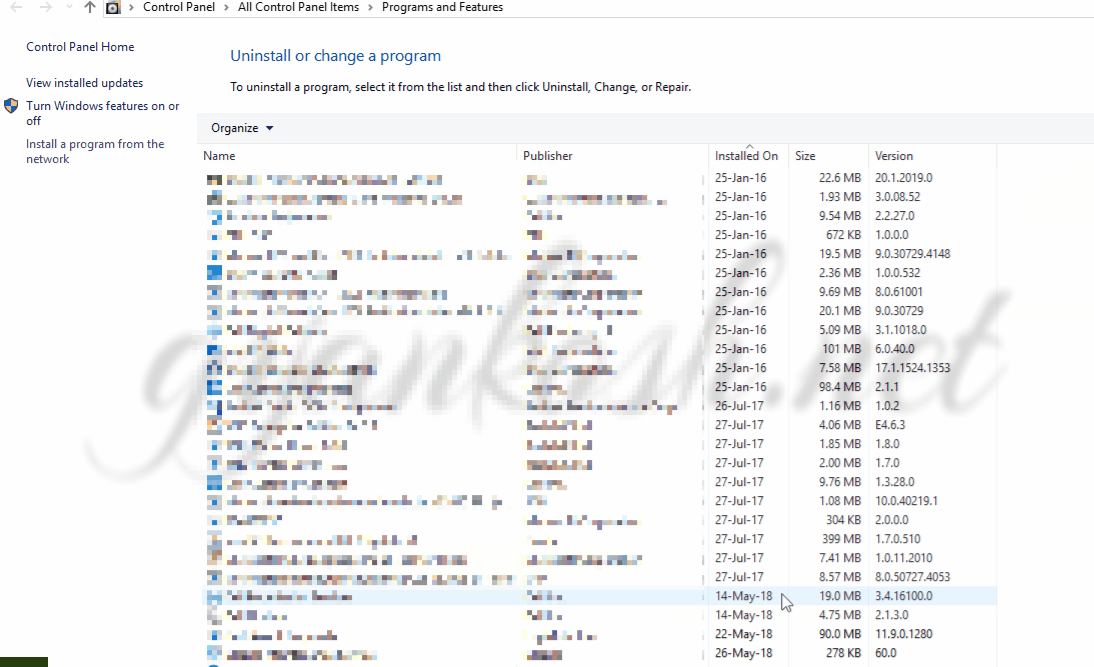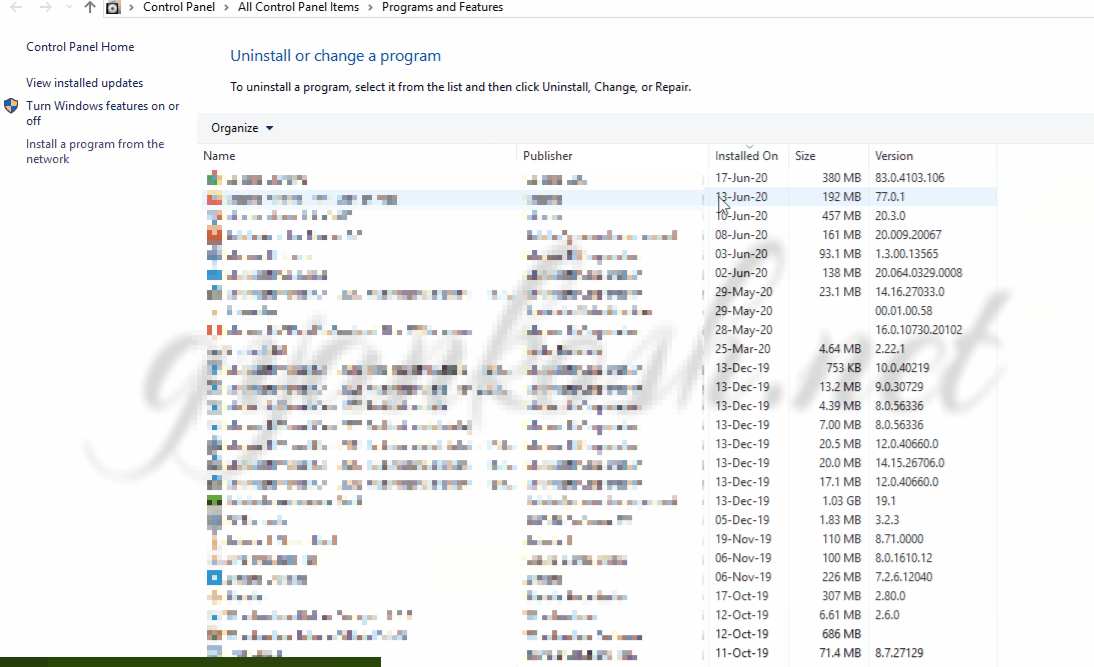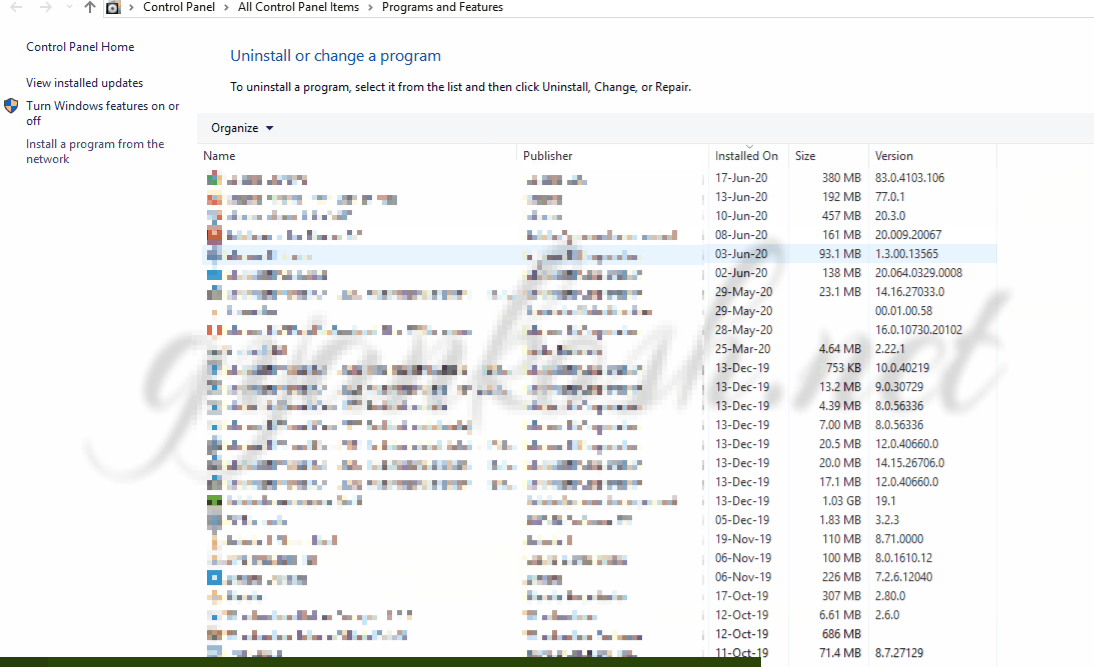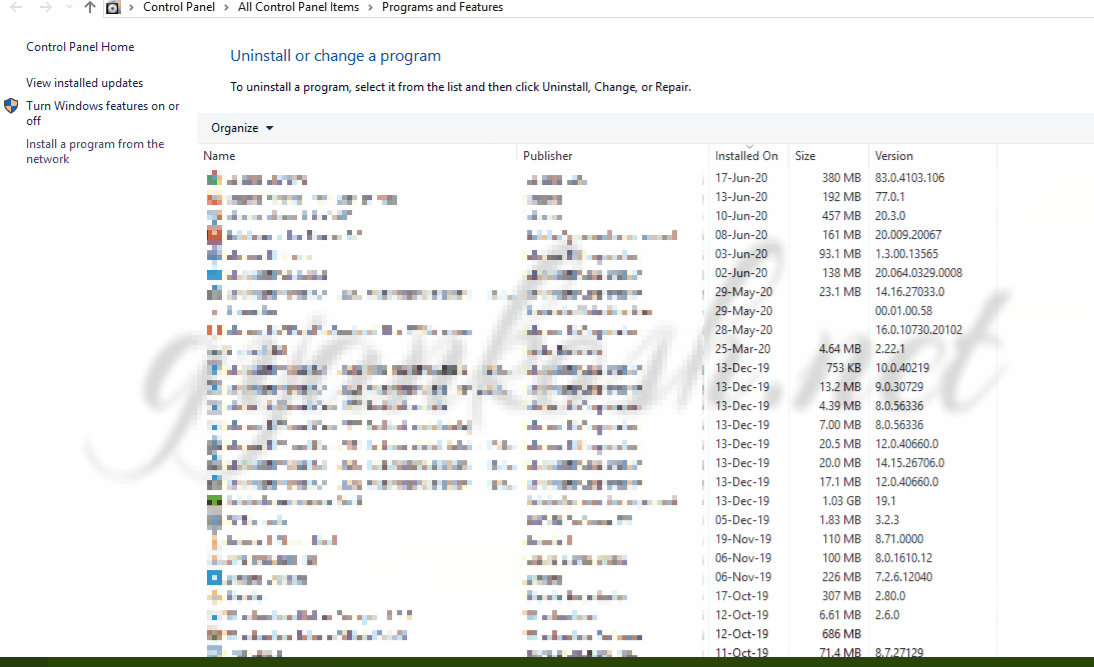
- Check out the programs installed on the date of infection.
- The VIRUS NAMES are strange something like vwwwwwwwww.exe or anything which makes no sense. PUBLISHER will be not known or blank.
- Uninstall the application immediately.
STEP 3: CLEANING THE REGISTRY
Windows registry contains many variables and values which are used by the windows in real time. The culprit softwares update these values and force their services to be in operation.
FOLLOW THE STEPS:
- Go to run and type “regedit”. [It’ll open the registry editor. Before this Windows will ask you about if we want to make changes to system. Press Yes]
- REGISTRY EDITOR WILL OPEN AS SHOWN IN THE PICTURE BELOW.
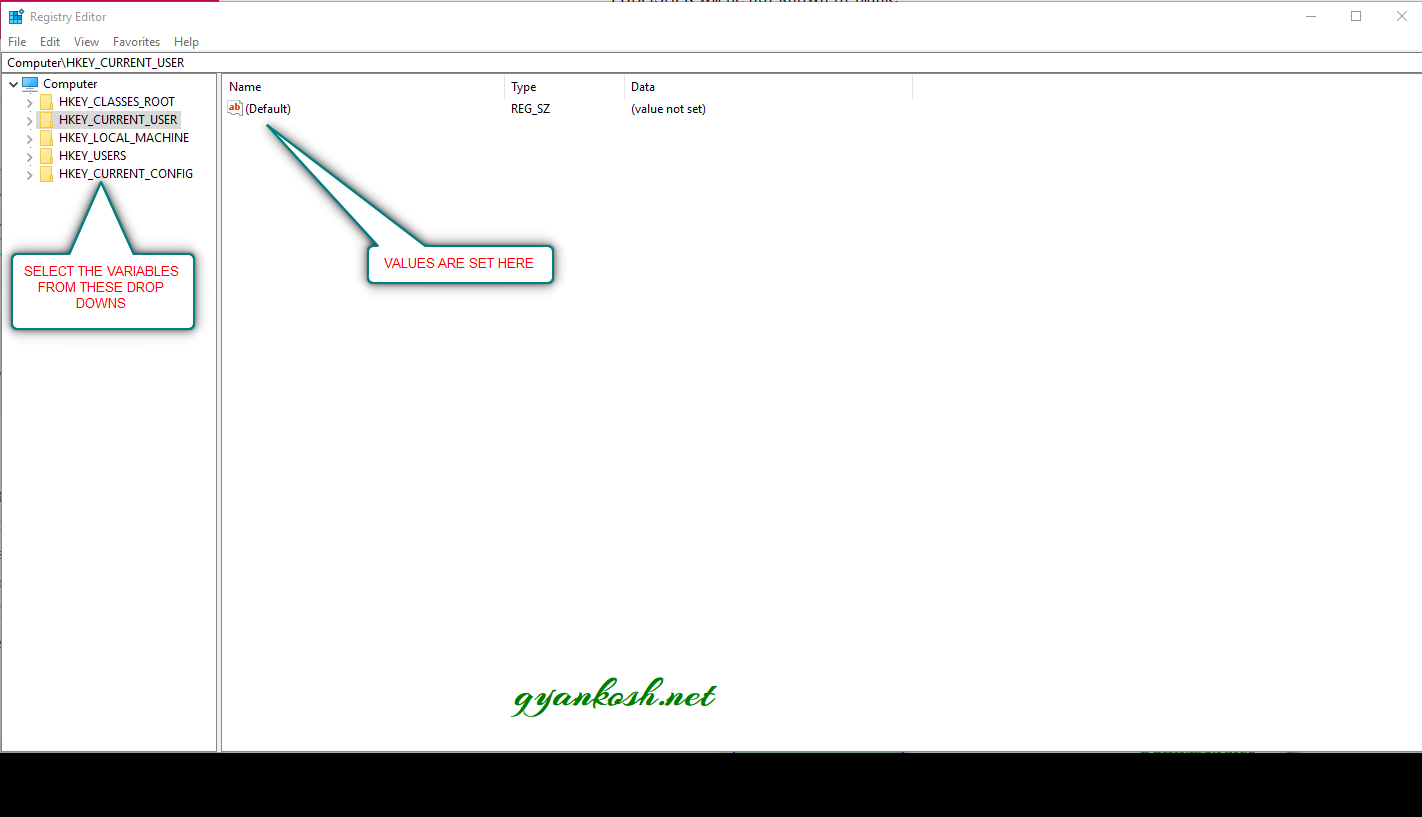
On the left hand side is the structure . We navigate through the structure to reach the variable we want to edit.On the right hand side , the variable list is displayed when we select the left side.Follow the steps to remove the suspicious entries.
- Go to HKEY_LOCAL_MACHINE>SOFTWARE>MICROSOFT>WINDOWS>CURRENT VERSION>RUN.
- Have a look at all the entries.
- Search for any doubtful entry which has a strange name or is being executed from C:\User\default\appdata….
- RightClick and Delete it. [NO NEED TO DELETE ALL THE ENTRIES. CHECK THE ADDRESS AND YOU’LL BE SURE IF THE ENTRY IS VIRUS GENERATED OR NOT. THERE ARE A FEW ENTRIES FROM THE SYSTEM32 FOLDER. NO NEED TO TOUCH THEM.
After the entries have been deleted from HKEY_LOCAL_MACHINE, we need to repeat the same procedure for HKEY_CURRENT_USER.Go to HKEY_CURRENT_USER>SOFTWARE>MICROSOFT>WINDOWS>CURRENT VERSION>RUN
- Search for any doubtful entry which has a strange name or is being executed from C:\User\default\appdata….
- RightClick and Delete it. It can be same as the previous one.
- CLOSE THE REGISTRY EDITOR.
STEP4: CLEANING THE TEMP FOLDER
Windows have a TEMP folder which contains the files which are created by the softwares for a brief period while we are using the software and those files are needed.Many times the virus is put in the temp folder and it keeps operating from there. So let us clean the temp folder too. FOLLOW THE STEPS TO CLEAR THE TEMP FOLDER OF WINDOWS.
- Go to RUN.
- Type %TEMP% in the field and click ok or reach USER>APPDATA>LOCAL>TEMP
- It’ll open the temp folder window.
- Select all and delete. There can be a few files which are in use and windows asks you to skip. Skip them.
STEP4: CLEANING THE ERRONEOUS START UP FILES
One more step is to check and clean the START UP FILES if virus has put the initiation of the virus service there.Follow the steps to clean the erroneous startup files.
- Go to C:\Users\MAIN_USER\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup and scan the folder. There will be a file named desktop.ini. If there are any suspicious files like a “.dll” or any other file delete them immediately.
STEP 5: RESTARTING THE WINDOWS NORMALLY
Now we have cleaned all the places where the virus can affect and it is time to reopen the windows normally. You must remember that we had opted for the SAFE BOOT. So let us reverse the process and opt for the normal boot.
FOLLOW THE STEPS TO SET THE WINDOWS FOR NORMAL BOOTING
- Press WINDOWS KEY+R, which will open RUN COMMAND.
- Type “msconfig” in the field and press OK.
- A prompt will open from the windows “ASKING THAT IT IS A SYSTEM UTILITY. IF YOU WANT TO CONTINUE. ” PRESS YES.
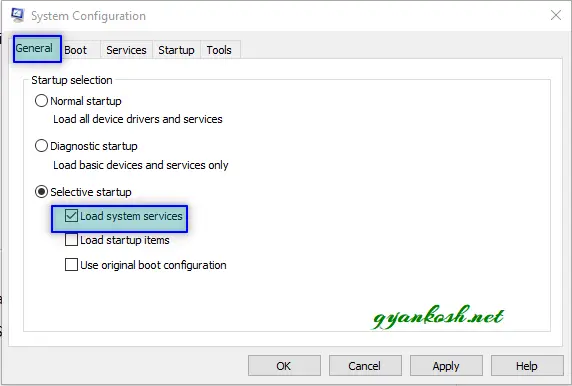
- In the system configuration dialog box, go to BOOT TAB and go to BOOT OPTIONS [marked in the picture below].
- Uncheck SAFE BOOT .
- In addition to this we can have one more safety so that if even after cleaning something is left. Go to GENERAL TAB>SELECTIVE STARTUP and choose LOAD SYSTEM SERVICES only. Uncheck rest of the options.
- Click APPLY.
- CLICK RESTART.
The windows should start normally and the culprit services won’t be there to further create any problem.ALTHOUGH THIS PROCESS WAS FOR RANSOMWARE BUT YOU CAN USE THIS FOR OTHER VIRUSES, TROJANS ETC. TOO TO SAVE YOURSELF FROM THE LOSS OF DATA.Now, let us try to recover the data which is already encrypted by the ransomware.
RECOVERING THE DATA ENCRYPTED BY THE RANSOMWARE
Now, we have eliminated the RANSOMWARE MANUALLY but now we are left with a bigger problem which is the data that has been already encrypted by the ransomware.
So, in this field a great work has been done by Michael Gillespie of Emsisoft Ltd – www.emsisoft.com who has launched a free decrypting tool for the victims like us known as EMSISOFT DECRYPTOR FOR STOP DJVU which will work for the USAM TOO.
Unfortunately, this tool will not work for every victim as it can only recover files encrypted by 148 of the 160 variants. The remaining variants are still under progress and it is quite possible that in future solution comes for those also.
*My problem was solved by this decryptor. Let us see how to use this.
TOOL FOR DECRYPTION– CLICK HERE TO DOWNLOAD.
HOW TO USE THE DECRYPTOR TO GET RID OF USAM RANSOMWARE
STEP 1: STARTING THE TOOL
- Click the link mentioned above to download the decryptor.
- By clicking the link, it’ll download a file which can be saved on your computer.
- Double Click the file.
- Windows will ask if you want to allow the file to make changes to device, don’t worry and click yes.
- The following screen will follow warning you about the risk of using the tool.
- IF YOU WAN’T TO CONTINUE, CLICK YES.
AS ALL THE SYSTEM TROUBLESHOOTING TOOLS DIRECTLY WORK WITH THE SYSTEM FILES, ALWAYS BE CAUTIOUS ABOUT THE WORST OUTCOME, WHICH IS LOSING YOUR DATA. SO ALWAYS KEEP A COPY OF DATA BEFORE TRYING ANY OF THE PROCEDURE.
STEP 2: KNOW THE DECRYPTOR TOOL AND DECRYPT.
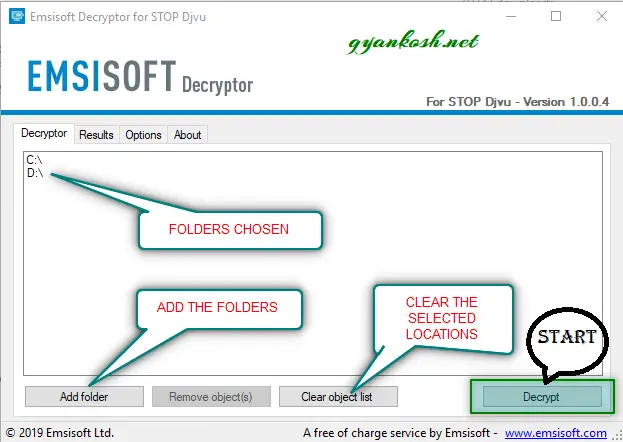
- Take a look at the picture below. This is the first screen of the STOP DJVU DECRYPTOR TOOL.
- On the bottom left is the ADD FOLDER button. Click it and choose the locations to be added. By default all the drives are already added. If you want to try the tool first [ which is recommended], press CLEAR OBJECT LIST first and then add a small folder using the ADD FOLDER button.
- After choosing the folder , it’ll show the chosen location in the central pane as shown in the picture with FOLDERS CHOSEN caption.
- CLICK DECRYPT. [THE TOOL DO NEED AN ACTIVE INTERNET CONNECTION TO GET THE DATA FROM THE SERVER. NO NEED TO PANIC, JUST LET IT DO ITS JOB. WHEN I WAS TRYING, I STOPPED THE CONNECTION AND IT STOPPED WORKING.]
- The tool would start working and start decrypting the files.
- If successful, it’ll place the file in the same location of the original file.
- The result tab will show all the logs.
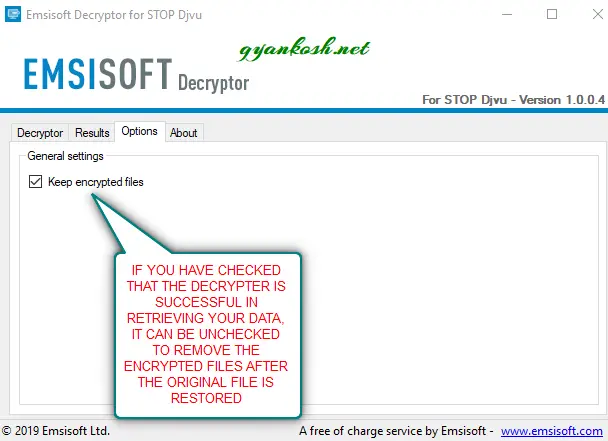
STEP 3: DECIDING IF WE WANT TO KEEP THE ENCRYPTED FILE OR NOT
- If we are successful in retrieving the data, we have an option to keep or remove the encrypted file.
- The problem with keeping the encrypted file is that it’ll double the space used.
- My experience-I had around 1000 GB data and was not having space to double the data by keeping the encrypted file, so took this risk and chose the option, NOT TO KEEP THE ENCRYPTED FILE.
Follow the steps to choose to keep encrypted files or not in STOP DJVU DECRYPTOR TOOL.
- We consider that the tool is already opened.
- Go to OPTIONS TAB.
- Uncheck KEEP ENCRYPTED FILES if you want to remove the encrypted files and only keep the decrypted files.
IF THE SAMPLE CHECK OF THE DECRYPTION IS SUCCESSFUL , WE CAN SELECT THE COMPLETE DRIVES AND START THE TOOLS WITH AN INTERNET CONNECTION.It does take time but if it works, its worth it.
UPDATE 1: HOW TO BE SAFE FROM RANSOMWARE
If you are not affected by this kind of virus [or any kind of virus] yet, that’s a good news. But what about the future??
It is very obvious that we all want to be safe from these kind of problems. If you have never been through, mark my words, the feeling is not good. We always gather so much of the digital data from very rare resources, sometimes we create data and most of the time it is official. It is very frightening when we find that our data is gone and can’t be recovered. If it is personal, you have to do that much of hundreds of hours of hardwork again. If it is official, you can imagine what can be the consequences.
So , we’ll discuss a few points or rather revisit[ because in fact, we all know these] few points by which we can be safe from any kind of viruses.
- Never visit the websites you don’t trust. These websites can come across your way mostly when you are trying find some specific audio, video or software etc. Google too warn you sometimes and on the spur of the moment, we ignore too but don’t ignore.
- Stop opening the links from the email unless it is well authenticated and expected. “Learn to ignore”.
- No clicking of messages from the mobile phones. It can cost you millions.
- Keep a good antivirus/antimalware software which is always updated. [ Buy good one . It is worth it.]
- Never TURN OFF your antivirus/antimalware.
- Mostly the virus comes through the torrents. We try to find the softwares, audios or videos on torrents. The criminals keep the virus in the form of executable files which we download from the torrents and after the download we execute them. We don’t get software but virus. We need to be very careful while executing the .exe files. It is always preferred to go to legit resources for softwares.
- Keep your system clean as possible. Just keep the softwares which we use.